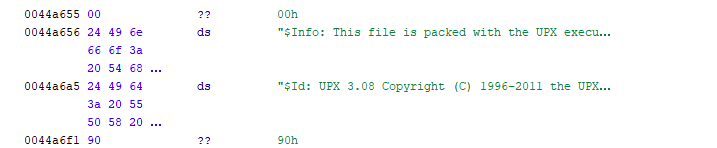
UPX compressed
This one seems to be right in our alley, this just asks to reverse the binary! So it will probably a cluster fuck of operations that won’t make any sense. When opening I was correct, this seems to be some obfuscated code. But what I did notice while looking diagonally through the file was that this seems to be packaged by UPX which is a compressor for binaries.

We can decompress this easily with UPX.
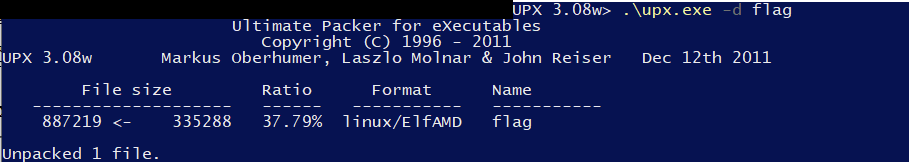
When doing this… the file will be unpacked in the original file!
Now we open this new file in Ghidra and suddenly we have a more readable binary!
00401164 PUSH RBP
00401165 MOV RBP,RSP
00401168 SUB RSP,0x10
0040116c MOV EDI=>s_I_will_malloc()_and_strcpy_the_f_004966 = "I will malloc() and strcpy th
00401171 CALL puts
00401176 MOV EDI,0x64
0040117b CALL malloc
00401180 MOV qword ptr [RBP + local_10],RAX
00401184 MOV RDX=>s_UPX...?_sounds_like_a_delivery_s_004966
0040118b MOV RAX,qword ptr [RBP + local_10]
0040118f MOV RSI=>s_UPX...?_sounds_like_a_delivery_s_004966 = "UPX...? sounds like a deliver
00401192 MOV RDI,RAX
00401195 CALL thunk_FUN_00400326
0040119a MOV EAX,0x0
0040119f LEAVE
004011a0 RET