As I am back on a computer without my tools I searched for another challenge that could only be done without any reversing. I came upon coin1, which seems to announce a simple game. The challenge is… solve it a hundred times in a minute.
Yeah… that seems to be needing an exploit or a program. As one of the hints is to run it on the pwnable server itself it seems you need to automate it. The rules you must take in regard.
---------------------------------------------------
- Shall we play a game? -
---------------------------------------------------
You have given some gold coins in your hand
however, there is one counterfeit coin among them
counterfeit coin looks exactly same as real coin
however, its weight is different from real one
real coin weighs 10, counterfeit coin weighes 9
help me to find the counterfeit coin with a scale
if you find 100 counterfeit coins, you will get reward
FYI, you have 60 seconds.
- How to play -
1. you get a number of coins (N) and number of chances (C)
2. then you specify a set of index numbers of coins to be weighed
3. you get the weight information
4. 2~3 repeats C time, then you give the answer
- Example -
[Server] N=4 C=2 # find counterfeit among 4 coins with 2 trial
[Client] 0 1 # weigh first and second coin
[Server] 20 # scale result : 20
[Client] 3 # weigh fourth coin
[Server] 10 # scale result : 10
[Client] 2 # counterfeit coin is third!
[Server] Correct!
- Ready? starting in 3 sec... -
N=610 C=10After playing with it I got a good idea of how it all worked and as you can enter multiple coins which will give a sum of the weight we could easily implement a binary search to solve this (I totally forgot the name of it while programming, when reading a blog always assume the person writing it spends more time searching for extra info to appear much smarter than he/she actually is).
Here is my Python implementation.
import socket
import re
with socket.socket(socket.AF_INET, socket.SOCK_STREAM) as s:
s.connect(("pwnable.kr", 9007))
while True:
data = s.recv(1024).decode("utf-8")
print(data)
info = re.search("^N=(?P<TotalCoins>\d{1,4}) C=(?P<Tries>\d{1,2})", data)
if info:
start = 0
end = int(info.group('TotalCoins'))
print(str(end))
for coin_try in range(int(info.group("Tries"))):
print("Try=>" + str(coin_try))
print(" ".join([str(x) for x in range(start, (start+end) // 2)]))
s.sendall(bytes(" ".join([str(x) for x in range(start, (start+end) // 2)]) + "\n", 'utf-8'))
data = int(s.recv(1024).decode('UTF-8'))
if data % 10:
end = (start + end) // 2
else:
start = (start + end) // 2
s.sendall(bytes(str(start) + "\n", 'utf-8'))
print(s.recv(1024).decode('UTF-8'))When running it I suddenly understood what they meant with running it on the server locally. The latency to the server was making it impossible for my script to solve this.

Running it on the server by opening python3 interpreter and just pasting the script gave results!
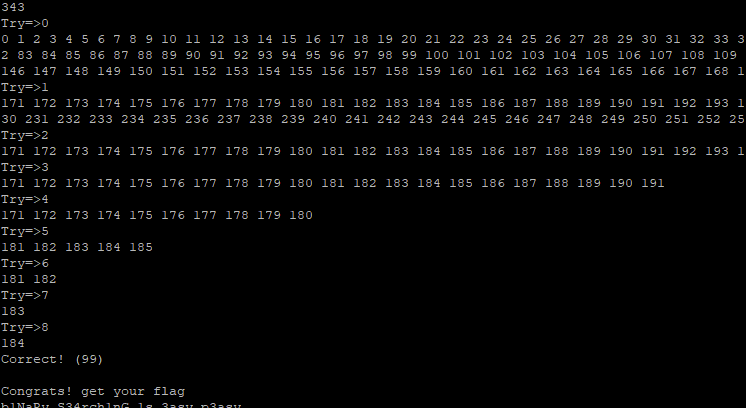
Now, as I do with more challenges, I look up other people results and solutions and noticed many using pwntools for this challenge. Maybe I should have done that as well but their is also a reason for using only standard libraries and that is… python3 module pwntools isn’t installed on the pwnable.kr servers.
< Home